- Why [24]7.ai
- Products
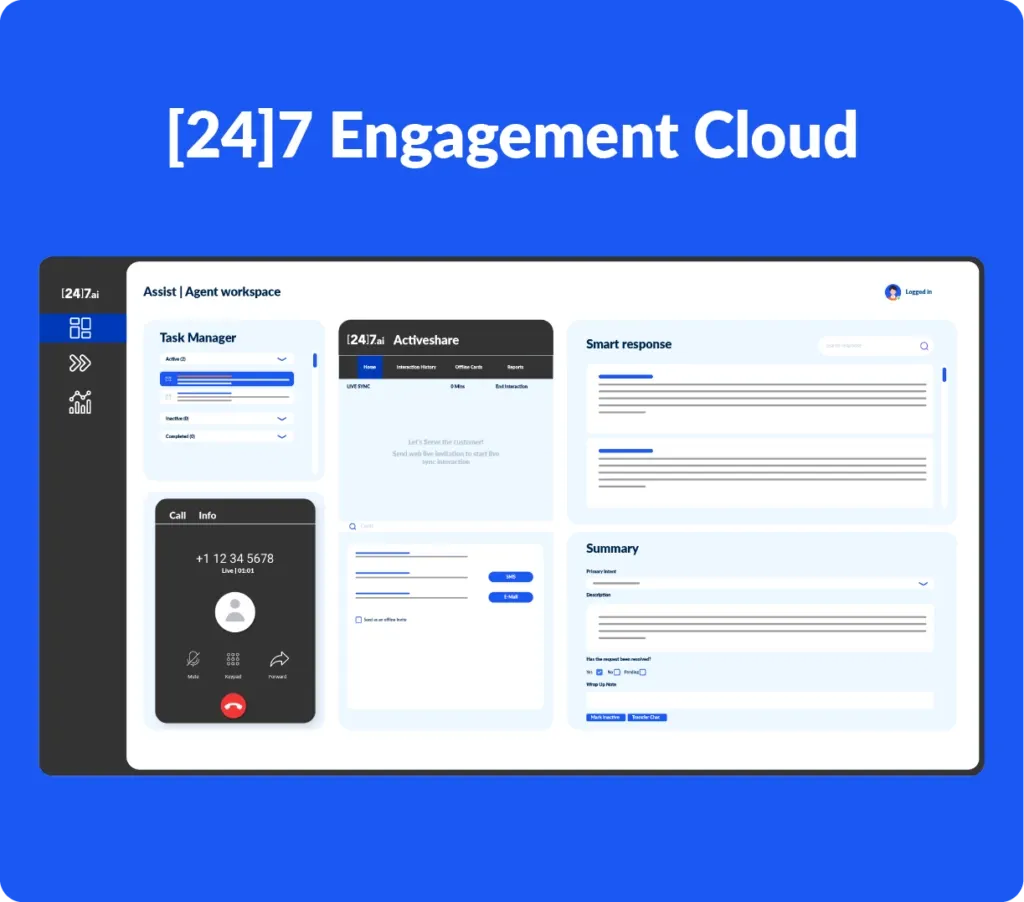
[24]7 Engagement Cloud, an AI-powered omnichannel CX platform, equips you to excel at every stage of the customer journey, from the very first interaction to building enduring relationships. A complete package that helps you acquire new customers, nurture existing ones, and drive long-term retention – all on a single, unified platform.
Discover how our platform empowers customers, agents and contact center leaders to deliver exceptional CX: - Services
Crafting Unforgettable Customer Experiences
Go beyond meeting expectations and cultivate customer loyalty. We are passionate CX specialists dedicated to crafting unforgettable experiences. Leverage a powerful blend of expertise, teamwork, and cutting-edge technology to transform your CX strategy. - Solutions
End-To-End CX Management
Explore by Use Case
US Retailer Transforms CX with [24]7.ai Managed Customer Engagement
Gold Awards at US Customer Experience Awards, 2024
- Company
Explore [24]7.ai
Explore Locations
- Insights
- Careers
Work @ [24]7.ai
Work Locations
- Product Login and Support
- Contact Us
Prioritizing Your Trust: [24]7.ai Trust Center
At [24]7.ai, we prioritize the security and privacy of your data. This section details our commitment to data privacy, from compliance with regulations to ongoing improvement. Learn more about how we safeguard your information across our website, platform, and various data privacy laws.
Website Privacy
[24]7.ai respects your privacy and protects any personal information you provide on this website. This includes data like your name, email address, and anything that could identify you. We use reasonable safeguards to keep your information secure and only use it for legitimate business purposes. We never sell your personal information. Read More
Platform Privacy
[24]7.ai protects your privacy on provide software platforms, applications, and data analysis systems (collectively, the “[24]7.ai Platform”). We collect and process End User’s information which may include Personal Information and browsing information to with permission to provide clients with relevant product information, assistance in completing transactions and resolving customer services issues. We never sell your information and follow strict security standards. For control over your data, contact the website you visited. Read More
CCPA
California residents have rights under the CCPA to access, delete, and opt-out of the sale of their personal data. We collect data like name and email to provide services and support. We share this data with service providers under strict contracts that protect your privacy. Visit our CCPA page to learn more and submit requests. Read More
GDPR
[24]7.ai protects your privacy under the EU’s GDPR law. We use minimal personal data (like IP address) to help clients improve customer experiences. We follow strict security standards and give you control over your information. Contact us to learn more about your GDPR rights. Read More
[24]7 Connect Privacy
The [24]7.ai Connect app provides notifications and self-service options for employees and approved non-employees. We collect some personal data (like email address) to run the app and keep your information secure. This data is used only for authorized purposes within [24]7.ai. You can opt-out by uninstalling the app. Contact us with any privacy questions. Read More




We conduct internal evaluations of security, privacy, risk, and security posture against the following frameworks:
- National Institute of Standards and Technology (NIST) SP 800-53 Revision 4/Revision 5, Security and Privacy Controls for Information Systems and Organizations (NIST 800-53): This framework provides a systematic approach for a broad range of public and private sector organizations to implement a comprehensive set of security and privacy safeguards. These measures apply to all types of computing platforms, including cyber-physical systems, mobile and cloud systems, general-purpose computing systems, industrial/process control systems, and Internet of Things (IoT) devices.
- NIST Cybersecurity Framework (CSF) Version 1.1: Initially developed for industries critical to national and economic security, the NIST CSF has proven to be flexible and adaptable. It is now voluntarily adopted by large and small companies and organizations across all sectors, as well as by federal, state, and local governments.
At [24]7.ai, security isn’t an afterthought, it’s ingrained in everything we do. We understand the critical nature of your data and digital experiences, and we’re committed to safeguarding them with the most robust measures available.
Product Security
We follow Shift-Left Security Methodology where security validations are introduced in early stages of Software Development Life-Cycle(SDLC). Our development teams are constantly trained and equipped with the latest secure coding practices to build robust and reliable products. Products go through Architecture review, Threat modelling, Peer-review, Static Application Security Testing(SAST) and Dynamic Application Security Testing(DAST) which ensures security vulnerabilities are addressed in every stage of product development. This multi-layered approach ensures the security of your data is prioritized at every stage.
Data Security
We maintain secure and redundant backups of your data for complete availability and recoverability. Your data always remains protected, both in storage (at rest) and during transmission (in transit).
Application Security
We follow Secure Application Development and Deployment Standard that prioritizes security throughout the development process. Static Code analysis tools are configured to continuously scan for and address potential security issues within our applications. Each application undergoes through Vulnerability Assessment and Penetration Testing(VA/PT) before applications are made available on production.
Network Security
We leverage a secure Virtual Private Cloud (VPC) environment to isolate and protect your data within our network. Advanced systems (IDS/IPS) constantly monitor our network for suspicious activity, safeguarding against potential threats. Network security firewalls act as a rigorous first line of defence, filtering and monitoring all traffic entering and leaving our systems.
Access Control
We implement robust access controls to ensure only authorized personnel can access specific data based on their roles (need to know basis). Comprehensive logs track all user interactions and data access attempts.
Enterprise Security
Our rigorous internal audit program continuously evaluates and improves the effectiveness of our security controls. We prioritize employee awareness through regular security training programs. Thorough security background checks are conducted on all employees during the hiring process.




At [24]7.ai, we take data privacy and security very seriously. That’s why we adhere to the highest industry standards and regulations, including HIPAA, PCI DSS, ISO 27001 and AICPA. These rigorous frameworks ensure your data is protected according to strict compliance guidelines. Additionally, we undergo independent audits to verify our adherence to these standards, providing you with an extra layer of assurance.
PCI DSS

We adhere and follow the PCI DSS standard to secure credit card information. This industry-wide standard applies to any business that handles cardholder data. We offer resources to help our customers comply with PCI DSS requirements.
Read MoreAICPA SOC 2

[24]7.ai SOC 2 compliance is verified by independent third-party auditors, which ensures we have met the criteria for managing customer data based on five AICPA Trust Service Principles and Criteria: Security, Availability, Processing Integrity, Confidentiality and Privacy.
Read MoreISO 27001

We hold ISO/IEC 27001:2013 certification, a rigorous international security standard. This ensures we systematically manage information security risks, implement robust controls, and have a continuous improvement process – all verified by independent auditors.
Read MoreHealth Insurance Portability and Accountability Act (HIPAA)

We are compliant with Health Insurance Portability and Accountability Act (HIPAA). We ensure our compliance with all HIPAA Rules (Privacy, Security, and Breach Notification) and adhere to the regulated Administrative, Physical, and Technical Safeguards.
Read More
At [24]7.ai, trust is paramount. We prioritize responsible AI deployments and secure
your data with advanced encryption, access controls, and clear usage guidelines. You
own and control your data, and we empower you to manage it.
Data Privacy and Protection
Your data is in safe hands. We prioritize data privacy and take comprehensive measures to ensure it is always treated with the utmost care.
Data Encryption
All data transmitted, stored and processed within [24]7.ai
applications and environments, including interactions with LLMs, is encrypted
using state-of-the-art encryption methods and protocols. This ensures that the
data of our clients remains confidential and secure during transit, while at rest,
and in use.
Granular Access Controls
We implement stringent access controls such as RBAC (Role Based Access Controls), allowing only authorized personnel to
access specific datasets with least privilege and need-to-know security principles. This ensures that individuals of [24]7.ai and/or clients/partners have access only to the data necessary for their roles, minimizing the risk of
unauthorized exposure.
Purpose-Limited Data Usage
We are committed to using the data of our clients solely for the purposes explicitly defined in our agreements. At [24]7.ai
our systems are designed to process and leverage data only in ways that align with the intended functionalities and benefits outlined in our solutions.
Data Ownership and Control
You, retain ownership and control over the data you share with us. [24]7.ai, as data processor, would be able to help in meeting various data privacy and compliance norms such as CCPA, GDPR, Privacy Shield, and APEC CBPR. Our privacy program is assessed annually by a third-party assessor.
Security
Security is the foundation of everything we do. We continuously adapt our industry-
leading measures to safeguard the integrity of your data.
Data Security Audits and Assessments
We follow a proactive approach in conducting regular security audits and assessments to identify and address potential vulnerabilities in our systems. This allows us to stay ahead of
evolving security threats and continuously fortify our defences.
Audits
We adhere to the highest industry standards and regulations. We undergo independent audits to verify our adherence to standards like PCI,
HIPPA, ISO, and SOC2
Vendor Management and Assessments
At [24]7.ai our third-party vendors, including LLM providers undergo thorough assessments to ensure they adhere to our stringent security and privacy standards. This diligence extends to every entity involved in the [24]7.ai’s product ecosystem.
Incident Response Preparedness
Our incident response methods arerobust and well-defined. In the unlikely event of a security incident, our team is prepared to respond promptly, efficiently, and in accordance with industry best-
practices to minimize any potential impact.
Regular Security Training
At [24]7.ai our personnel are continuously trained on the latest security practices and are well-versed in identifying and addressing potential security risks. This commitment extends to all job levels of
our organization, ensuring a culture of security awareness.
Continuous Monitoring and Threat Detection
Our systems undergo
continuous monitoring by the Security Operations Center team. Threat detection mechanisms are in place to promptly identify and mitigate any suspicious activities. This proactive stance enables us to address and respond to potential security incidents in real-time.
Safety of the LLM
Your privacy and safety are our top priorities. We do not
use your data for training purposes, and your interactions with our LLMs remain confidential. Our automated systems continuously evaluate prompts and responses against our strict content policy, filtering out high-severity
content to ensure a safe and responsible AI experience.
Frequently Asked Questions
When providing services to a customer, [24]7.ai may transfer personal data outside of EEA, Switzerland and UK in its capacity as processor. The General Data Protection Regulation (GDPR) has been incorporated into UK’s domestic legislation, and therefore the data transfer mechanism permitted under the GDPR for transfers of personal data.
When providing services to a customer, [24]7.ai may transfer personal data outside of EEA, Switzerland and UK in its capacity as processor. The General Data Protection Regulation (GDPR) has been incorporated into UK’s domestic legislation, and therefore the data transfer mechanism permitted under the GDPR for transfers of personal data.
When providing services to a customer, [24]7.ai may transfer personal data outside of EEA, Switzerland and UK in its capacity as processor. The General Data Protection Regulation (GDPR) has been incorporated into UK’s domestic legislation, and therefore the data transfer mechanism permitted under the GDPR for transfers of personal data.
When providing services to a customer, [24]7.ai may transfer personal data outside of EEA, Switzerland and UK in its capacity as processor. The General Data Protection Regulation (GDPR) has been incorporated into UK’s domestic legislation, and therefore the data transfer mechanism permitted under the GDPR for transfers of personal data.
When providing services to a customer, [24]7.ai may transfer personal data outside of EEA, Switzerland and UK in its capacity as processor. The General Data Protection Regulation (GDPR) has been incorporated into UK’s domestic legislation, and therefore the data transfer mechanism permitted under the GDPR for transfers of personal data.